Use case objectives
Armies are made up of many entities deployed throughout the country, at sea with naval forces, and even in operational sites abroad. During peacetime—and especially in times of conflict— headquarters require the ability to centrally monitor the status of their forces. By their very nature, the information systems used in the armed forces are highly heterogeneous, so the use of the IDMEFv2 pivot format and the Safe4SOC architecture makes it possible to offer a centralized view of the armed forces’ cyber and physical situation.
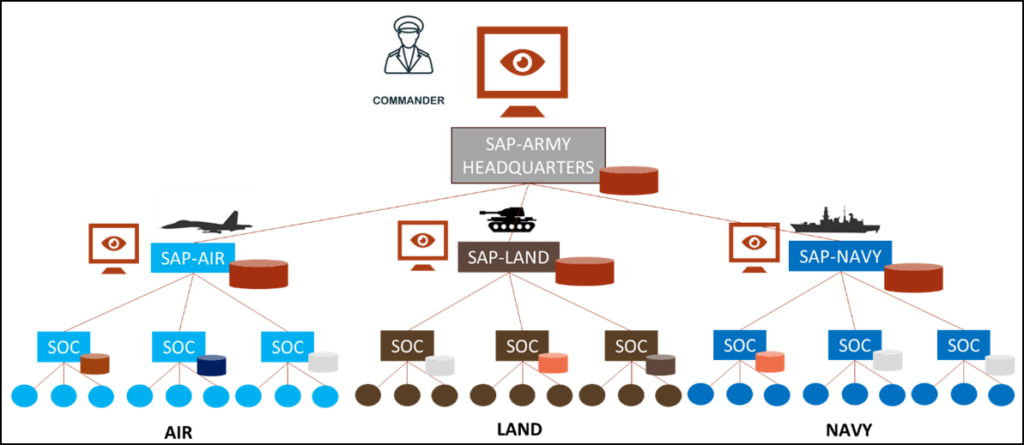
Safe4Soc Army Use Case.
The diagram above represents a typical army force organization. Multiple army corps (here Air, Land and Navy) under the authority of the Army General Head Quarters. Each army corps is composed of many bases. Each base and their local IT systems or applications do not use the same security monitoring tools and format. All this infrastructure must be monitored at army level and general headquarters must have access to a Situational Awareness Platform (SAP).
In addition, army forces systems are composed of cyber systems and a lot of physical systems (for instance transport or weapons, drones, etc.) whose availability and security must be monitored. The combination of the concepts IDMEFv2, the Safe4Soc SIEM, and the IS-GW thus respond to this problem.
The need for interoperability becomes even more critical when European armies collaborate under a Framework Nation leading multiple national forces.
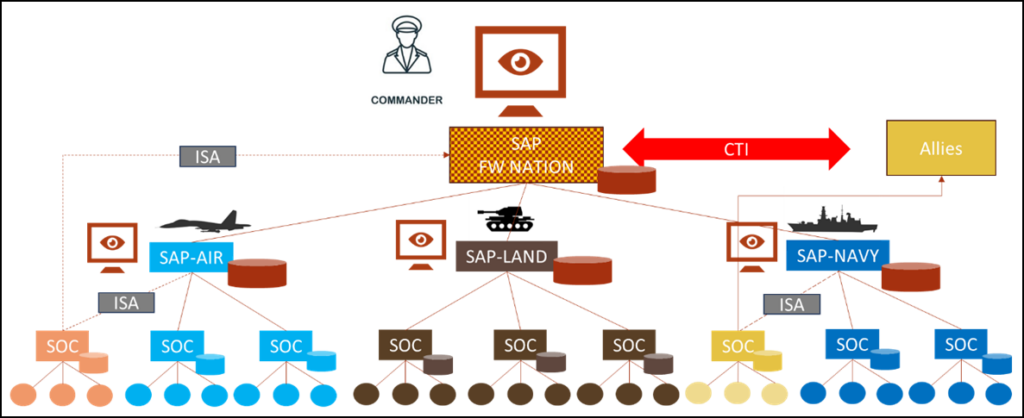
Safe4Soc Framework Nation Concept (NATO).
The concept of an Information Sharing Agreement (ISA) is important for this use case. Even during collaboration, allied forces may choose to filter the information they share with the Framework Nation, while sharing it directly with their own Armed Force Central Command.
This architecture offers the following services:
- Real-time monitoring of the security situation at operational bases.
- Hierarchical monitoring at several levels: base, army (land, air, sea), headquarters.
- In the case of European forces, interconnection between allied armies in presence (thanks to the IDMEFv2 standard).
- Thanks to centralized analysis of all alerts and their corresponding incidents, similar attack scenarios can be detected and prevented, and CTI can be created.
The army use case highlights all specific features provided by S4S and the ability to centralize all types of incidents. For armed forces, both cyber and physical incident information are equally crucial as well as natural hazard information as external conditions have a direct impact on troops and external operations. Using IDMEFv2 data concerning cyber-security, physical security, and operational availability can be centralized and monitored efficiently.
Example
Centralized monitoring is already a recognized need in forces such as the French Army.
The land army is composed of 150 entities, from large bases to much more modest installations, including in theaters of operation. The air army is composed of 30 bases; the navy is composed of 10 major ports and 200 boats. All those forces use hundreds of applications developed in multiple programs and often embedded their own security monitoring tools.
In theory, most of those asset monitoring should be accessible to the higher authority. In peace time, the needs are similar to a large corporation, in war time or as we live actually “cold war” ages any major incident is important and should be quickly centralized. For instance, drone sights in military areas or structural power outages, as they might indicate sabotages, etc.
Security
The army typically requires more security than everyday business cases. For instance, the confidentiality, data encryption, authentication and integrity protection are standard demands. Additionally, permanent availability of data in real-time, is another standard demand.
The Safe4Soc Information Sharing Gateway which serves as backbone of the Safe4Soc architecture offers a high level of configurable security which is already sufficient for most army deployments for the transmission of alerts:
- Mutually authenticated connection setups using a dedicated Public Key Infrastructure (PKI), to neglect spoofing attacks of sending or receiving entities.
- State-of-the-art encryption to provide confidentiality and integrity for data transmission.
- The application of filtering, enrichment or anonymization features to alert data to precisely configure an acceptable level of data protection.
- Direct transmission to offer real-time data processing.