Use Case Objectives
The nation’s interests are ensured by several critical operators (energy, telecommunications, transport, etc.) which are prime targets in the event of conflict, as we are currently seeing in Ukraine, where Russia regularly targets energy infrastructures. This hybrid war can take many forms, both physical and cyber. Rapid reporting of significant incidents to national authority is crucial and required by the various regulations such as, for instance, NIS or CER.
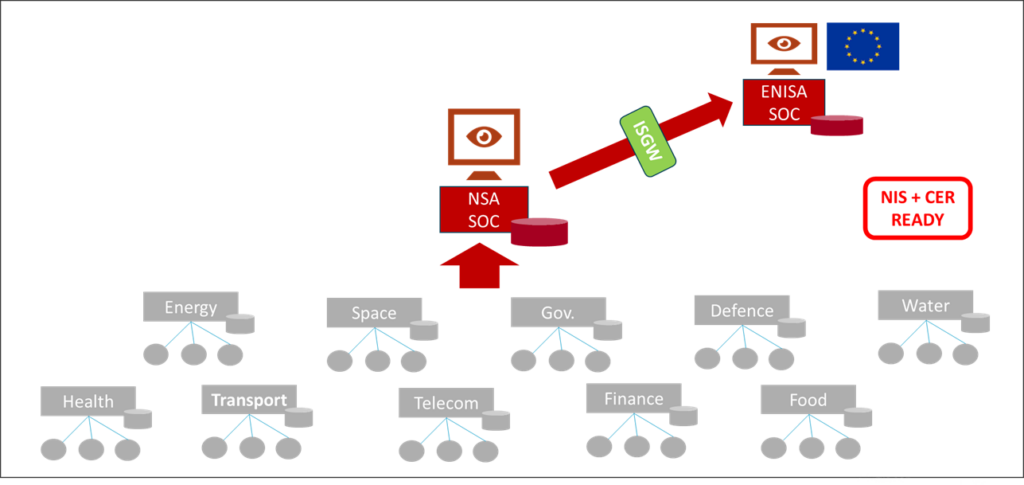
Critical Operators Use Case
In this context, a Safe4Soc infrastructure will offer:
- A set of SIEM Gateways translating alerts from propriatory SIEMs (QRadar, Splunk, RSA, etc.) to IDMEFv2
- A highly secured connection between critical operators and their National Security through the mechanism of the Information Sharing Gateway, for filtering and securing data. The ISGW’s objective is to ensure that each SOC/NOC/PSIM connected to the central system shares only the information necessary for shared monitoring without disclosing sensitive information. This filtering is based on an Information Sharing Agreement and takes place within the gateway, which removes, anonymizes, or encrypts information according to the agreements between the two parties. This functionality responds, among other things, to the needs for partitioning and the need to know that centralized hypervision systems for our vital systems could require, particularly in the case of multi-nation systems.
- A pivot format IDMEFv2 offering the capability to report technical information about incidents in a shared format and thus being able to store, compare, analyze, and correlate that information in real time.
- A SIEM console (Concerto SIEM) gathering all majors’ incidents from all critical operators in the same tool.
- The possibility to detect combined and/or complex hybrid attacks through the use of AI and/or classical detection/correlation/statistics.
- The easy capacity to share all (or parts due to the ISGW filters) of incident information with other countries in Europe.
European directives currently require reporting major incidents within 24 hours. An incident is detected, a first analysis is conducted, and operators fill a non-standardized form to inform authorities. Safe4Soc allows much faster reporting, providing direct connection between systems without waiting for local human analysis. This complementary approach supports collaborative detection in near real-time, which can be crucial in certain scenarios (e.g., unidentified drones) where speed is essential.
Examples
Combined or complex attacks directed to critical operators would probably been driven by high class hackers in the service of a hostile country. Therefore, it is difficult to anticipate this kind of attacks, but the real time centralization might still be very useful.
What is happening with Russia now gives good examples of what European critical infrastructure must fear and prepare to fear. These kinds of attacks might be cyber or physical or combined.
The recent overflight of unidentified drones over European infrastructure is a good example of threat detection information that needs to be centralized and shared as soon as possible. Ukraine is experiencing every night massive drone attacks on its critical infrastructure as well as cyber-attack attempts. The Safe4Soc architecture won’t stop those kinds of massive and simultaneous attacks but would certainly help faster reaction and protection. Especially when those attacks are targeted toward multiple Europeans countries who don’t share yet some standard format to ease, structure and accelerate communication.